Vip Client Which Generates A Token Key

This page will explain you how to generate a Security Token and how you can use it to authenticate against our API.
What is an API Token?
Security information: API tokens are like passwords, they allow total access to your account, do no share them! If you believe one of your tokens was compromised, delete it and create a new one.
- These tokens offer a method to establish secure server-to-server authentication by transferring a compact JSON object with a signed payload of your account’s API Key and Secret. When authenticating to the Zoom API, a JWT should be generated uniquely by a server-side application and included as a Bearer Token in the header of each request.
- Aug 22, 2016 Video guide to generate API Key and OAth Client ID for WordPress plugins Embed Any Document Plus and Drivr for Google Drive. Google APIs: Generate API Key and OAth Client ID. Generate Google.
- Oct 16, 2018 A JWT is an open standard (RFC 7519) for using JSON to transmit information between parties as digitally signed string tokens. They can be signed with the HMAC algorithm or using a public/private key pair using RSA or ECDSA. To say this another way: JWTs are a JSON token that is a URL-safe, compact, and self-contained string.
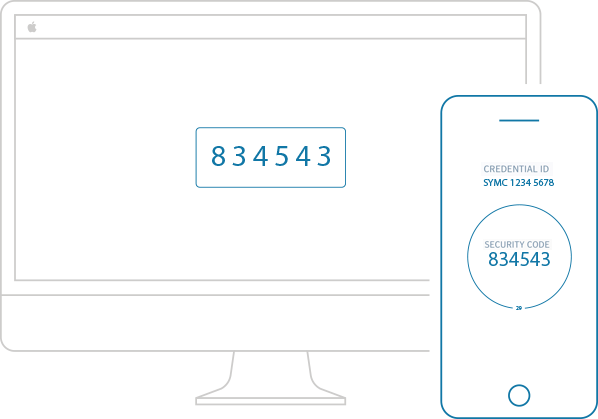
A security token is a free software application (Symantec VIP Access) or physical device that generates random security codes used in the TFAS process. It provides the “key” you need to access Allstate’s two. Ordering a new Symantec VIP hardware key (Paypal Security Token) sadly my old Symantec Validation & ID Protection hardware key card only shows 'noBatt' when trying to generate a code. So, I need a replacement for it. Home; Get Started - VIP Access for Desktop; Troubleshoot - VIP Access for Desktop; Get Started - VIP Access for Mobile; Troubleshoot - VIP Access for Mobile.
API tokens are unique identifiers associated with your Scaleway account and consist of an Access Key and a Secret Key. The Secret key is required to authenticate against our API and will only be displayed when you create the token. Make sure to take a note of it and to keep it secret.
What are Access Key and Secret Key?
Before you can start using our API, you need to generate a Security Key and Access Key pair. Consider the Access Key as a login, and the secret key as a password. A token is the pair of those 2 values.
- An Access Key can identify a token.
- It’s not a sensitive piece of information.
- The Secret Key is the value that can be used to authenticate against the API (the value used in X-Auth-Token HTTP-header).
- The secret must stay secret and not given to anyone or publish online.
Each Scaleway account can have several tokens (so several pairs of access-key + secret). Several tokens are useful to give different applications access to the same Scaleway account. However, you remain in control and you can revoke access to any application individually.
C# Generate Token
Tokens that have been generated before the introduction of the Secret Key can be used without restriction. For Security reasons it is recommended to use Secret Keys whenever possible.
How to generate an API Token?
- Open the drop-down menu on your account name and click on Credentials.
- To generate a new token, click on Generate new token in the Tokens section of the page.
- The Access Key and the Secret Key will show on your screen. Take a note of the Secret Key as it will not be recoverable.
- Execute a command through our API (e.g. List your servers) with your API Token
Client Authentication
When a confidential OIDC client needs to send a backchannel request (for example, to exchange code for the token, or to refresh the token) it needs to authenticate against the {project_name} server. By default, there are three ways to authenticate the client: client ID and client secret, client authentication with signed JWT, or client authentication with signed JWT using client secret.
Client ID and Client Secret
This is the traditional method described in the OAuth2 specification. The client has a secret, which needs to be known to both the adapter (application) and the {project_name} server.You can generate the secret for a particular client in the {project_name} administration console, and then paste this secret into the keycloak.json file on the application side:
Client Authentication with Signed JWT
This is based on the RFC7523 specification. It works this way:
The client must have the private key and certificate. For {project_name} this is available through the traditional
keystorefile, which is either available on the client application’s classpath or somewhere on the file system.Once the client application is started, it allows to download its public key in JWKS format using a URL such as http://myhost.com/myapp/k_jwks, assuming that http://myhost.com/myapp is the base URL of your client application. This URL can be used by {project_name} (see below).
During authentication, the client generates a JWT token and signs it with its private key and sends it to {project_name} inthe particular backchannel request (for example, code-to-token request) in the
client_assertionparameter.Jan 21, 2018 Varun January 21, 2018 Java: How to get all keys by a value in HashMap? Search by Value in Map 2018-01-21T16:15:15+05:30 collections, HashMap, java, Java Interview Questions No Comment In this article we will discuss how to search into a Map by value and fetch associated keys to the given value. Java generate all key values for a map. Apr 09, 2020 The Map interface of Java Collections offers a method called entrySet. It returns all the entries or key-value pairs of the map in a Set. The idea is to iterate over this entry-set and return the key for which the value matches the supplied value.
{project_name} must have the public key or certificate of the client so that it can verify the signature on JWT. In {project_name} you need to configure client credentials for your client. First you need to choose
Signed JWTas the method of authenticating your client in the tabCredentialsin administration console.Then you can choose to either:Configure the JWKS URL where {project_name} can download the client’s public keys. This can be a URL such as http://myhost.com/myapp/k_jwks (see details above). This option is the most flexible, since the client can rotate its keys anytime and {project_name} then always downloads new keys when needed without needing to change the configuration. More accurately, {project_name} downloads new keys when it sees the token signed by an unknown
kid(Key ID).Upload the client’s public key or certificate, either in PEM format, in JWK format, or from the keystore. With this option, the public key is hardcoded and must be changed when the client generates a new key pair.You can even generate your own keystore from the {project_name} admininstration console if you don’t have your own available.For more details on how to set up the {project_name} administration console see {adminguide_link}[{adminguide_name}].
C# Generate Access Token
For set up on the adapter side you need to have something like this in your keycloak.json file:
Generate Token Php
With this configuration, the keystore file keystore-client.jks must be available on classpath in your WAR. If you do not use the prefix classpath:you can point to any file on the file system where the client application is running.